
Extreme Networks K-Series K6 Chassis
6-slot chassis offering up to a maximum of 144 triple-speed ports and (4) 10Gb uplinks

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
The Extreme Networks K-Series™ is the most cost-effective, flow-based switching solution in the industry. Providing exceptional levels of automation, visibility and control from the network edge to the small enterprise core, these flexible, modular switches significantly reduce operational costs while still offering premium features.
The K-Series is built upon the Extreme Networks CoreFlow2 custom ASIC. This cornerstone switching technology provides greater visibility into critical business applications and the ability to enable better controls to meet the Service Level Agreements (SLAs) demanded by the business.
Designed to address the challenges associated with a growing demand for access to new applications and services, the K-Series protects businesses traffic and supports changing operational needs. This includes the consumerization of IT and "bring your own device" programs that require more robust location, identification, visibility and overall management capabilities. The K-Series is uniquely suited to intelligently manage individual user, device and application conversations, as well as to provide the visibility and management to troubleshoot connectivity issues, locate devices, and ensure protection of corporate data.
- Versatile, high density edge to small core switching with flexible connectivity and power options reduces cost of ownership
- Advanced automated network provisioning maximizes the efficiency and reliability of supporting new IT services such as virtualized desktops
- Integrated visibility, granularity and control delivers significant cost savings and premium security for mission critical networks
- Easy to deploy access controls and prioritization provides more robust location, identification and overall management capabilities including support for "bring your own device" programs
The K-Series makes forwarding decisions and enforces security policies and roles while classifying/prioritizing traffic at wire speed. All I/O modules provide the highest Quality of Service (QoS) features for critical applications such as voice and HD video even during periods of high network traffic load while also proactively preventing Denial of Service (DoS) attacks and malware propagation.
The K-Series implements an industry-leading, flow-based switching architecture to intelligently manage individual user and application conversations - far beyond the capabilities of switches that are limited to using VLANs, ACLs, and ports to implement role-based access controls. Users are identified and roles are applied to ensure each individual user can access their business-critical applications no matter where they connect to the network. K-Series policy rules combined with deep packet inspection can intelligently sense and automatically respond to security threats while improving reliability and quality of the user experience.
A significant differentiator for the K-Series is the ability to collect NetFlow data at wire-speed providing total visibility into network resource consumption for users and applications. The K-Series joins the S-Series as the only enterprise switches to support multi-user, multimethod authentication on every port - absolutely essential when you have devices such as IP phones, computers, printers, copiers, security cameras, badge readers, and virtual machines connected to the network.
These new modular switches deliver flexible connectivity, premium features and integrated security that enable the network to quickly adapt to changing business requirements.
Features:
Multi-layer packet classification - enables the delivery of critical applications to specific users via traffic awareness and control
- User, port, and device Level (Layer 2 through 4 packet classification)
- QoS mapping to priority queues (802.1p & IP ToS/ DSCP) up to 11 queues per port
- Multiple queuing mechanisms (SPQ, WFQ, WRR and Hybrid)
- Granular QoS/rate limiting
- VLAN to policy mapping
Switching/VLAN services - provides high performance connectivity, aggregation, and rapid recovery services
- Extensive industry standards compliance (IEEE and IETF)
- Inbound and outbound bandwidth rate control per flow
- VLAN services support
- Link aggregation (IEEE 802.3ad)
- Multiple spanning trees (IEEE 802.1s)
- Rapid reconfiguration of spanning tree (IEEE 802.1w)
- Provider Bridges (IEEE 802.1ad), Q-in-Q Ready
- Flow setup throttling
- DHCP Server
IP Routing - provides dynamic traffic optimization, broadcast containment and efficient network resilience
- Standard routing features include static routes, RIPv2, RIPng and Multicast routing support (DVMRP, IGMP v1/v2/v3), Policy Based Routing and Route Maps and VRRP
- Licensed routing features include OSPF v2/v3, VRF and PIM-SM
Security (User, Network and Management)
- User security
- Authentication (802.1X, MAC, PWA+ and CEP), MAC (Static and Dynamic) port locking
- Multi-user authentication/policies
- Network security
- Access Control Lists (ACL) basic and extended
- Policy-based security services (examples: spoofing, unsupported protocol access, intrusion prevention, DoS attacks limits)
- Management Security
- Secure access to the K-Series via SSH, SNMP v3
Management, Control and Analysis - provide streamlined tools for maintaining network availability and health
- Configuration
- Industry-standard CLI and web management support
- Multiple firmware images with editable configuration files
- Network Analysis
- SNMP v1/v2c/v3, RMON (9 groups) and SMON (rfc2613) VLAN and Stats
- Port/VLAN mirroring (one-to-one, one-to-many, many-to-many)
- Unsampled NetFlow on every port with no impact on system switching and routing performance
- Automated set-up and reconfiguration
- Replacement I/O module will automatically inherit previous modules configuration
Feature-Rich Functionality
Examples of additional functionality and features that are supported by the Extreme Networks K-Series:
- NetFlow - Provides real-time visibility, application profiling and capacity planning
- LLDP-MED - Link Layer Discovery Protocol for Media Endpoint Devices enhances VoIP deployments
- Flow Setup Throttling - (FST) effectively preempts and defends against DoS attacks
- Node & Alias Location - Automatically tracks user and device location and enhances network management productivity and fault isolation
- Port Protection Suite - Maintain network availability by ensuring good protocol and end station behavior
- Flex-Edge Technology - Provides advanced bandwidth management and allocation for demanding access/edge devices
Flow Setup Throttling (FST) is a proactive feature designed to mitigate zero-day threats and Denial of Service (DoS) attacks before they can affect the network. FST directly combats the effects of zero-day and DoS attacks by limiting the number of new or established flows that can be programmed on any individual switch port. This is achieved by monitoring the new flow arrival rate and/or controlling the maximum number of allowable flows.
In network operations, it is very time consuming to locate a device or find exactly where a user is connected. This is especially important when reacting to security breaches. Extreme Networks K-Series modules automatically track the network's user/device location information by listening to network traffic as it passes through the switch. This information is then used to populate the Node/Alias table with information such as an end-station's MAC address and Layer 3 alias information (IP address, IPX address, etc.). This information can then be utilized by Extreme Networks NMS Suite management tools to quickly determine the switch and port number for any IP address and take action against that device in the event of a security breach. This node and alias functionality is unique to Extreme Networks and reduces the time to pinpoint the exact location of a problem from hours to minutes.
For organizations looking to deploy Unified Communications, the Extreme Networks K-Series combines policy-based automation with support for multiple standards-based discovery methods, including LLDP-MED, SIP and H.323, to automatically identify and provision UC services for IP phones from all major vendors. K-Series switches also provide dynamic mobility for IP clients; when an IP phone moves and plugs in elsewhere in the enterprise network, its VoIP service provisioning, security and traffic priority settings move with it, with none of the typical manual administration required for moves, adds and changes.
The K-Series also supports a comprehensive portfolio of port protection capabilities, such as SPANguard and MACLock, which provide the ability to detect unauthorised bridges in the network and restrict a MAC address to a specific port. Other port protection features include Link Flap, Broadcast Suppression and Spanning Tree Loop protection which protects against mis-configuration and protocol failure.
Extreme Networks K-Series Flex-Edge technology provides line rate traffic classification for all access ports with guaranteed priority delivery for control plane traffic and high-priority traffic as defined by the Extreme Networks policy overlay. In addition to allocating resources for important network traffic, prioritized bandwidth can be assigned on a per port or per authenticated user basis. Flex-Edge technology is ideal for deployment in wiring closets and distribution points that can often suffer from spikes in utilization that cause network congestion. With Flex-Edge technologies, organizations no longer have to fear a momentary network congestion event that would result in topology changes and random packet discards.
Benefits:
Business Alignment
- Ensures each end-user receives the information, services and applications needed to achieve their business goals through extensive network visibility and control capabilities
- Green and efficient power system modularity drives down power and cooling costs by providing optimal incremental power consumption
- Consistent end user experience and network protection by effectively allocating critical network services while blocking suspicious traffic
Operational Efficiency
- High-density, small form factor chassis provides up to (216) 10/100/1000 ports with (8) 10Gb uplinks in a standard rack, significantly reducing footprint costs
- Management automation and builtin resiliency features drive down operational costs and maximize uptime
- Automatically identifies and provisions new devices and services reducing IT deployment time
Security
- Reduces risk and simplifies network administration with built-in, not boltedon security
- Protects business traffic from malicious attacks and maintains information confidentiality, integrity and availability
- Extends network access control and security to existing edge switches and wireless access points, meeting the challenges associated with the consumerization of IT
Support and Service
- Industry-leading customer satisfaction and first call resolution rates
Standards and Protocols:
Switching/VLAN Services
Class of Service
Network Security and Policy Management
IETF and IEEE MIB Support
|
IP Routing Features
|
Management, Control and Analysis
Extreme Networks Network Management Suite
|
Specifications:
| K-Series Models | K6 | K10 |
|---|---|---|
| Performance/Capacity | ||
| Switching Fabric Bandwidth | 280 Gbps | 440 Gbps |
| Switching Throughput | 190 Mpps (Measured in 64-byte packets) | 299 Mpps (Measured in 64-byte packets) |
| Routing Throughput | 190 Mpps (Measured in 64-byte packets) | 299 Mpps (Measured in 64-byte packets) |
| Address Table Size | 32,000 MAC Addresses | 32,000 MAC Addresses |
| VLANs Supported | 4,096 | 4,096 |
| Transmit Queues | 11 | 11 |
| Classification Rules | 8,196/chassis | 8,196/chassis |
| Packet Buffering | 3.0GB | 4.5GB |
| Physical Specifications | ||
| Chassis Dimensions (H x W x D) | H: 22.15 cm (8.719") W: 44.70 cm (17.60") D: 35.546 cm (14") 5U |
H: 31.02 cm cm (12.219") W: 44.70 cm (17.60"") D: 35.546 cm (14") 7U |
| Host Memory and Flash | 1Gb DRAM 32 MB flash memory |
1Gb DRAM 32 MB flash memory |
| Environmental Specifications | ||
| Operating Temperature | +5 °C to +40 °C (41 °F to 104 °F) | |
| Storage Temperature | -30 °C to +73 °C (-22 °F to 164 °F) | |
| Operating Humidity | 5% to 95% relative humidity, non-condensing | |
| Power Requirements | 100 to 125 VAC, 12 A or 200 to 250 VAC, 7.6 A; 50 to 60 Hz (Max per power supply) | |
| Power over Ethernet Specifications | ||
| System Power |
|
|
| Standards Compliance |
|
|
| Agency and Standards Specifications | ||
| Safety | UL 60950-1, FDA 21 CFR 1040.10 and 1040.11, CAN/CSA C22.2 No.60950-1, EN 60950-1, EN 60825-1, EN 60825-2, IEC 60950-1, 2006/95/EC (Low Voltage Directive) | |
| Electromagnetic compatibility | FCC 47 CFR Part 15 (Class A), ICES-003 (Class A), EN 55022 (Class A), EN 55024, EN 61000-3-2, EN 61000-3-3, AS/NZ CISPR-22 (Class A). VCCI V-3. CNS 13438 (BSMI), 2004/108/EC (EMC Directive) | |
| Environmental | 2002/95/EC (RoHS Directive), 2002/96/EC (WEEE Directive), Ministry of Information Order #39 (China RoHS) | |
Hardware-Based High Availability Features
The K-Series includes many standard high availability features. These hardware-based high availability features allow the K-Series to be deployed in mission critical environments that require 24/7 availability.
The K-Series supports the following hardware-based high availability features:
- Passive chassis backplane
- Hot swappable fan trays with multiple cooling fans
- Hot swappable and load-sharing power supplies
- Multiple AC input connections for power circuit redundancy
- Up to 36 groups of eight Ethernet ports can be grouped together to create a multi-link aggregation group (LAG)
Solutions:
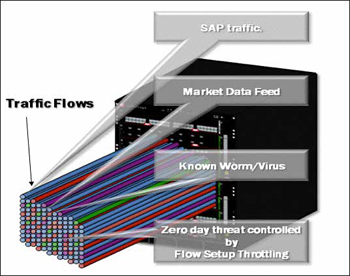 Distributed, Flow-Based Architecture
Distributed, Flow-Based Architecture
In order to ensure granular visibility and management of traffic without sacrificing performance, the Extreme Networks K-Series deploys a flowbased architecture. This architecture ensures that when a specific communications flow is being established between two end points, the first packets in that communication are processed through the multilayer classification engines in the switch and the I/O fabric module. In this process, the role is identified, the applicable policies are determined, the packets are inspected and the action is determined. After the flow is identified, all subsequent packets associated with that flow are automatically handled in the Extreme Networks ASICs without any further processing. In this way the Extreme Networks K-Series is able to apply a very granular level of control to each flow at full line rate.
Multi-User/Method Authentication and Policy
Authentication allows enterprise organizations to manage network access and provide mobility to users and devices. It provides a way to know who or what is connected to the network and where this connection is at any time. The Extreme Networks K-Series has unique, industry leading capabilities regarding types of simultaneous authentication methods. K-Series modules can support multiple concurrent authentication techniques, including:
- 802.1X authentication
- MAC authentication, which is a way to authenticate devices on the network using the MAC address
- Web-based authentication, also known as Port Web Authentication (PWA), where a user name and password are supplied through a browser
- CEP, also known as Convergence End Point, where multiple vendors VoIP phones are identified and authenticated; this capability provides great flexibility to enterprises looking to implement access control mechanisms across their infrastructure
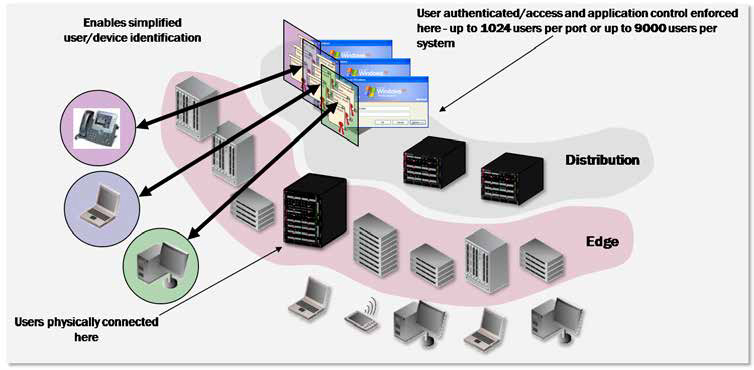
A significant additional feature of the K-Series is the capability to support multi-user authentication. This allows multiple users and devices to be connected to the same physical port and each user or device to be authenticated individually using one of the multi-method options (802.1x, MAC, PWA, or CEP). The major benefit of multi-user authentication is to authorize multiple users, either using dynamic policy or VLAN assignment for each authenticated user. In the case of dynamic policy, this is called Multi-User Policy. Multi-user port capacities with the K-Series are determined on a per port, per I/O module, and per multi-slot system basis.
Multi-user authentication and policy can provide significant benefits to customers by extending security services to users connected to unmanaged devices, third party switches/routers, VPN concentrators, or wireless LAN access points at the edge of their network. Using authentication provides security, priority, and bandwidth control while protecting existing network investments. The K-Series supports up to 8 users per port with a license option for 256 users per port. Total system capacity supports 1152 users on the K6 and 1920 users on the K10.
Dynamic, Flow-Based Packet Classification
Another unique feature that separates the Extreme Networks K-Series from all competitive switches is the capability to provide User-Based Multi-layer Packet Classification/QoS. With the wide array of network applications used on networks today, traditional Multi-layer Packet Classification by itself is not enough to guarantee the timely transport of businesscritical applications. In the K-Series, User-Based Multi-layer Packet Classification allows traffic classification not just by packet type, but also by the role of the user on the network and the assigned policy of that user. With User-Based Multi-layer Packet Classification, packets can be classified based on unique identifiers like "All Users", "User Groups", and "Individual User", thus ensuring a more granular approach to managing and maintaining network confidentiality, integrity, and availability.
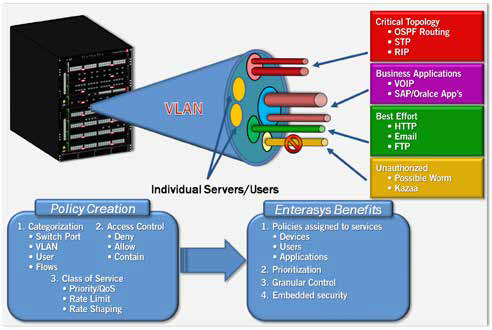
Network Visibility From High Fidelity NetFlow
Network performance management and security capabilities via NetFlow are available on Extreme Networks K-Series switch ports without slowing down switching and routing performance or requiring the purchase of expensive daughter cards for every module. Extreme Networks NetFlow tracks every packet in every flow as opposed to more typical statistical sampling techniques or restrictive appliance-based implementations. The value of unsampled, real-time NetFlow monitoring is the visibility into exactly what traffic is traversing the network. If something abnormal occurs it will be captured by NetFlow and appropriate action can be applied. Additionally, NetFlow can be used for capacity planning, allowing the network manager to monitor the traffic flows and volumes of traffic in the network and understand where the network needs to be reconfigured or upgraded. This saves time and money by enabling administrators to know when and where upgrades might be needed.
Network Traffic Monitoring - Port Mirroring
Port mirroring is an integrated diagnostic tool for tracking network performance and security that is especially useful for fending off network intrusion and attacks. It is a low-cost alternative to network taps and other solutions that may require additional hardware, disrupt normal network operation, affect client applications or may introduce a new point of failure into your network.
Port mirroring is highly scalable and easy to monitor. It is especially convenient to use in networks where ports are scarce. Ports that can be configured to participate in mirroring include physical ports, virtual ports and host ports-VLAN interfaces, and intrusion detection ports. With this feature, analyzing bi-directional traffic and ensuring connectivity between, for example, a departmental switch and its high speed uplink to a backbone switch becomes simple and cost effective process.
K-Series port mirroring relationships can be set on inbound traffic, outbound traffic, or both for up to 4 port mirrors consisting of one-to-one, one-to-many, many-to-one, IDS or policy mirrors.
Documentation:
Download the Extreme Networks K-Series Datasheet (PDF).

